In Azure database, security is managed through multiple-layers such as network layer, server layer and database layer. A secure blue print in deploying Azure SQL database starts with securing the surface area around the platform. These includes a secure connectivity to the Azure subscription through express-route, site-2-site or point-2-site VPN, preventing access to public IP address, disabling access to other Azure services, enable Network Security Group rules as well as enabling private link through private endpoint for connectivity between client and databases.
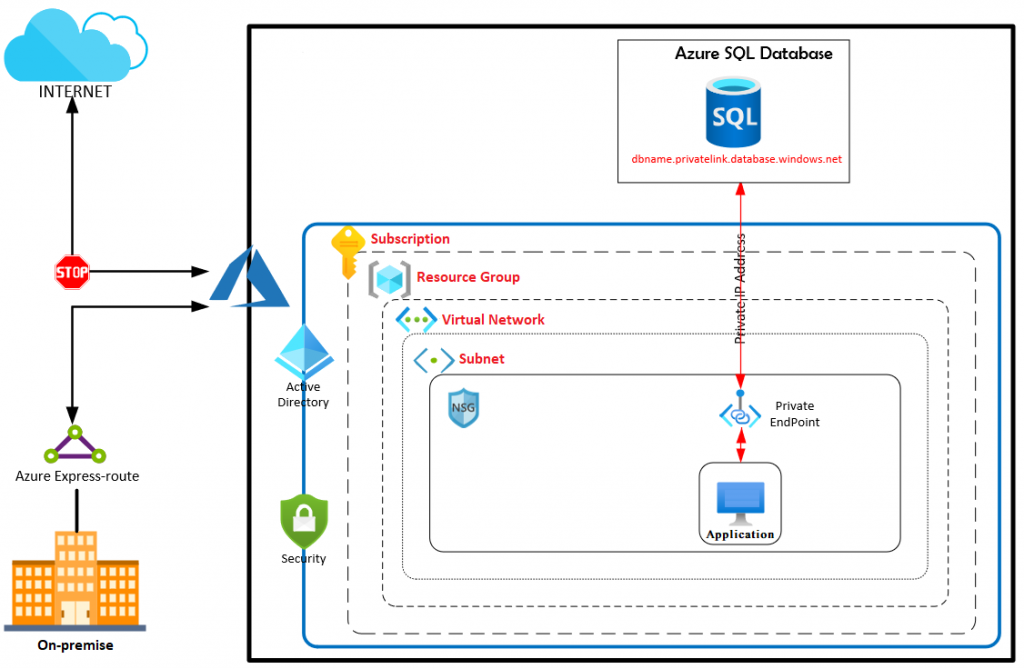
In Private End Point connectivity between client and database is based on IP address obtained from the local virtual network range. If Private End Point is not enabled in Azure virtual network properties, traffic flows through public endpoint on Public IP address obtained from Azure’s public IP range.
When using public link, access to the database is managed through virtual network, server level or database level firewall rule as shown below.
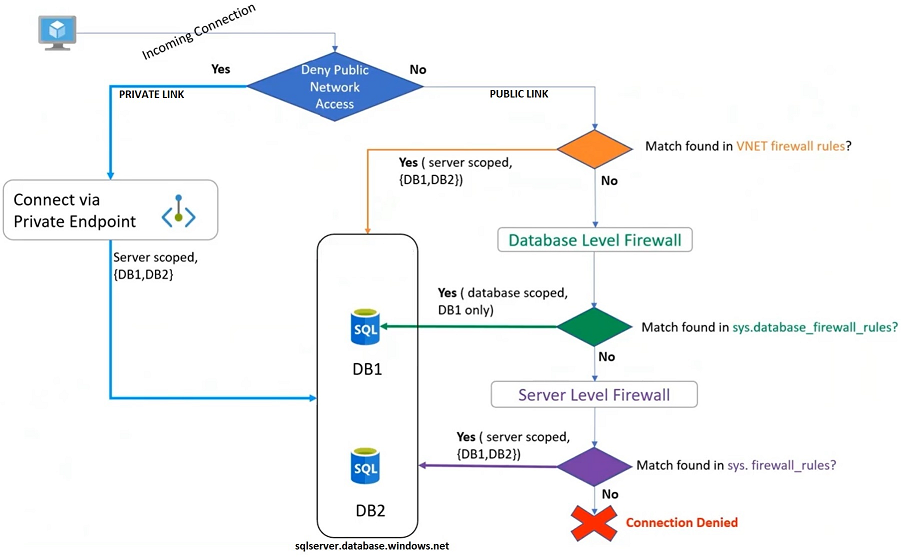
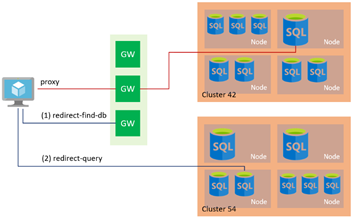
Azure SQL Connectivity Policy
Azure SQL database has three connectivity policies that impact how client connects, these policies depend on where the client request is coming from.
- Redirect: Once an initial connection is established from the database gateway, all subsequent connection to the database node is direct, bypassing database gateway, reducing the network latency and improving throughput, this is a recommended option for database services & it requires enabling outbound firewall rule for port number 1433 (Azure SQL Database Gateway) and port number range 11000-11999 (SQL Server Nodes)
- Proxy: Connections that are proxied via the Azure SQL database gateway (Port 1433) for initial and subsequent connections, increasing database latency and reducing throughput.
- Default: Clients connecting from within Azure uses Redirect is the default policy, and clients connecting from on-premise uses Proxy as the default policy.
Network Access Setting
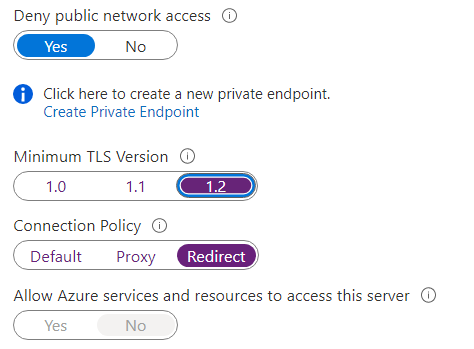
- Deny Public Network Access: To limit external IP addresses from accessing the database resource
- TLS Version: Set the TLS version to the latest version for secure communication, make sure all client has the same TLS version otherwise authentication attempt will not work
- Connection Policy: For better database connectivity performance select REDIRECT option, this will improve latency and throughput. Proxy option increases latency and throughput as all connections are proxied via the Azure SQL database gateway.
- Azure Services and Resources: Deny other Azure services from accessing this service from inside and outside the subscription
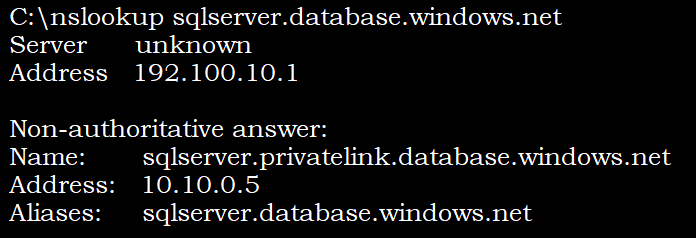
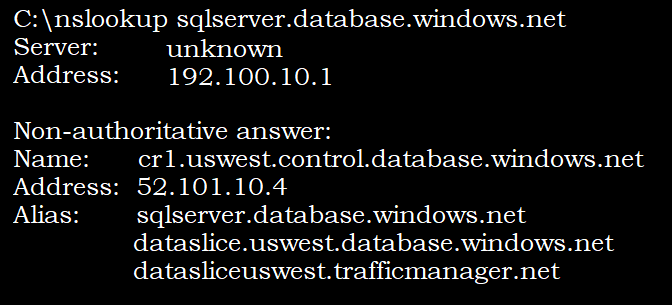
Verify pre and post Private EndPoint connection on the database server
- Pre-Private EndPoint nslookup shows external IP address of the Azure SQL database and associated Azure data center
- Post Private EndPoint nslookup shows Azure SQL database is using Private Link DNS alias with Private IP Address from the VNET range.